My First Valid Report and Reward in BugBounty
Hello Hackers,
Been a long time since i wrote anything. Today i will write about how i got my first valid report and reward.
Backstory
Allow me to introduce myself briefly. I am a cybersecurity and tech enthusiast currently studying as a student. My journey in cybersecurity began with TryHackMe, where I completed more than six pathways. Additionally, I joined platforms such as Hack The Box, CTF Challenge, PicoCTF, PortSwigger, PentesterLab, and others to further enhance my skills.
Despite possessing the necessary skills and knowledge to start bug bounty hunting, I hesitated due to a lack of confidence. I constantly felt inadequate compared to the amazing hackers out there (and even now, that feeling persists). However, I eventually discovered a way to access my college’s web application. You can read about it here.
This gave me the confident and motivation that i was lacking. After this i opened my account in hackerone and one another platform where i participated in one program. I was still not sure about it but submitted total 7 reports on single program

Even though all i got was duplicate but it really cheered me up. Then i tried to do something in hackerone where i reported total 3 reports where i got one duplicate, one informative and one need additional information(still working on this one).

I want to emphasize how incredible the PTN Community is, as it has been a source of immense knowledge, support, appreciation, and motivation for me. My senior brothers within the community have played a significant role in my growth and development. With their guidance, I truly felt that I was on the right path in my cybersecurity journey.
Moreover, I learned about the Dutch Government BBP, which not only presents researchers with opportunities to find vulnerabilities but also offers cool swag as rewards. This discovery further ignited my enthusiasm and determination to participate in bug bounty programs.

I wanted this too so i went to the repo where all the inscope domains of Dutch government BBP was stored. After viewing the overwhelming amount of domains i was so confused which domain to pick so i went with my instinct haha i picked up one domain, did recon, nothing found, moved to another domain same thing didn’t find anything interesting, next domain nothing there too i actually forgot how many domain i tried . I am saying all of this cause i want people mostly new comers to know that Bug Bounty is not easy thing to do where you just pick one target, hack it, report it and get $$$$$ rewards. Anyway after a huge number of unsuccessful attempt to get the cool swag i finally one target where i finally found:
Account Takeover Via CSRF bypass
But their response to my report was this:
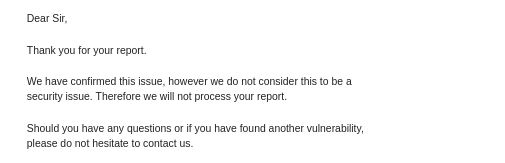
I didn’t get why my they said so it was heart breaking after so many trial and error i finally thought i got something and then boom it was not considered a security issue. Then after some time i moved onto another target i submitted another report

Then again moved to another target i got this

I don’t know how to describe it haha but i took it as positively as i could i kept reminding myself that i am doing good i am on the right path. Then i again moved onto another target which i got from the github repo for dutch government BBP inscope domains. And this is where our real story begins:
Real Story
I first visited the website that I found on the GitHub repository. It was an online platform specializing in online project websites, e-participation, and community with numerous functionalities and subdomains. It was overwhelming at first, but I continued exploring. Since I didn’t have a checklist for Bug Bounty, I simply aimed to find simple yet effective bugs that are often overlooked by professionals who consider them low-hanging fruits. (By this, I mean I tried to identify functional issues, business logic flaws, and misconfigurations, among others.) Like everyone else, I began with reconnaissance and captured all the requests in Burp Suite.
After completing the initial reconnaissance, I wasn’t sure if there were any vulnerabilities. Based on my knowledge and skills, I thought the website was quite secure. It had firewalls that seemed intact and effectively removed any suspicious user inputs. The subdomains appeared fine, there was rate limiting in place, and there were no misconfigurations. The website offered limited functionalities to visitors and didn’t require sign-ups. After considering all these factors, I felt uncertain about what to do next. I thought I had exhausted all possibilities.
Then, I decided to search for funny and suspicious API endpoints, and that’s when I stumbled upon a gem. I discovered a rather long API endpoint with numerous parameters. I selected it, sent it to repeaters, and examined the responses.
It’s response shocked me it was json response where i got personal user information.

Upon further investigation, I discovered that all of this information was being fetched for the blog section of the website. The response I received contained personal information of the writers who authored the blogs. It included sensitive details such as usernames, email addresses, and other personal information. Shockingly, there was no authentication mechanism in place. Therefore, anyone could access this URL and retrieve the sensitive details without any restrictions.
Here comes the interesting part. Despite realizing that this was a Personal Identifiable Information disclosure (PII Disclosure) vulnerability, I didn’t have high expectations for a response from them, but I still decided to report it. To my surprise, after 2–3 days, I received an email response that said the following:

I was quite surprised by the turn of events. Even though I had obtained the domain from the same repository that listed all the in-scope domains for the Dutch Government BBP (Bug Bounty Program), I still felt compelled to report the vulnerability. It was reassuring to know that they had a Vulnerability Disclosure Program (VDP) in place.
I wrote an email detailing all the information regarding the PII Disclosure vulnerability and sent it off. To be honest, I had zero expectations and simply wanted to fulfill my responsibility by reporting it.
However, the very next day, I received an email from the Chief Security Officer of the company.

I read it and i was like ok whatever. And exactly after 1 month of reporting this i got another email from the same officer

I was like whatdahell? haha i didn’t believe this at first but this was true after many unsuccessful attempts i finally got a valid report even though the report and the vulnerability i found were not praise worthy but they were definitely motivating.
That’s it, folks! This was my first bug bounty write-up, and it may not have involved cool vulnerabilities like SQL injection (SQLi), cross-site scripting (XSS), or others. It was simply a plain and simple bug that ended up being rewarded.
I wanted to emphasize that bug bounty hunting is not an easy task, and many people don’t share the struggles they face on their path to success. However, I believe it’s important to showcase my journey and the actual work I put into finding and reporting vulnerabilities.
Thank you for taking the time to read my write-up. This is just the beginning, and I’m excited for more rewards to come! Remember, keep hacking, keep learning, and keep helping others. ❤








